Sophos Phish Threat is available today in North America and will be available soon in other regions. Give it a try for free and let us know what you think! If you’re lucky enough to be attending RSA 2017, visit us at booth 3201 to see Sophos Phish Threat and many of our other industry-leading products in action. How do I allow Phish Threat in Sophos Email Gateway? Go to Sophos Central Dashboard Email Gateway Settings Click Inbound Allow / Block Click Add Click Add allow Enter the domain for the campaign as listed in Sophos Phish Threat Settings Sending domains and IPs. How do I allow Phish Threat in Reflexion?
Phishing has been a go-to tactic for criminals for decades but it remains as likely to keep your sysadmins awake at night as any 0-day or APT.

Even advanced threats like ransomware still rely on phishing to get into your network. Phishing works because it’s hard to defend against. The right software is a vital part of your strategy of defence-in-depth but ultimately it’s your staff that sit on the front line.
You know that ensuring your users can identify malicious emails and protect themselves against social engineering attacks is vital, but you also know that it’s really hard, right?
Wrong.
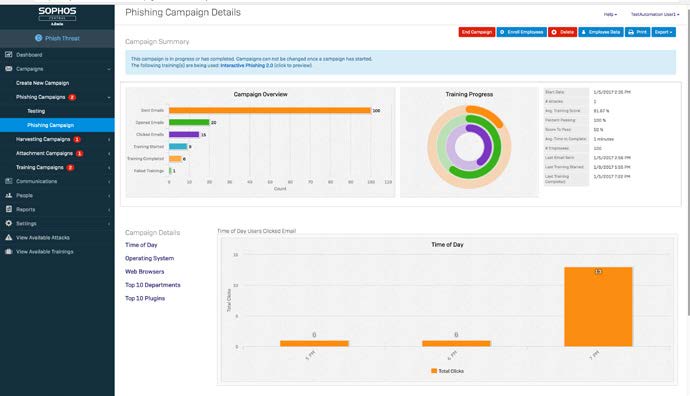
Sophos Phish Threat 2.0 is an enterprise-grade upgrade for your staff.
With 41% of IT professionals now reporting at least daily phishing attacks, but 62% of organizations still failing to test user awareness, Phish Threat is all about making it easy for you to test, assess and educate users to identify malicious emails. With it you can:
- Emulate basic and advanced phishing attacks
- Easily create relevant campaigns and send them in minutes
- Run effective training modules so users learn from their mistakes
- Get comprehensive reporting that covers individual to organizational levels
You get the benefits of our best ever reporting dashboard, along with full integration into Sophos Central, providing the simplest way to extend protection across your network and endpoints.
Sophos Central Login
Your end users get the seamless, interactive and engaging training they need to upgrade themselves against the latest phishing tactics.
Advanced, targeted phishing scams that impersonate well-known brands or VIPs within an organization are a big problem for security teams to deal with.
One common feature of these impersonation attacks, also known as Business Email Compromise, are that there are generally no malicious payloads or links to scan for. This makes such attacks extremely dangerous because they are notoriously difficult to detect and block.
Warning from the FBI
The FBI is warning organizations to be on the lookout for an increase in these BEC scams. Such scams abuse auto-forwarding rules in web-based email clients, allowing attackers to insert themselves into conversations by leveraging email addresses using domains with similar spelling to their victims’ real addresses.
A recent incident in August 2020 following this pattern of deception allowed attackers to obtain $175,000 from their victim. The FBI’s Internet Crime Complaint Center (IC3) reported BEC schemes resulted in more than $1.7 billion in worldwide losses in 2019.
Who can you trust?
Often making urgent requests for funds or sensitive data, 86% of impersonation emails assume the identity of a specific individual rather than a brand, according to SophosLabs.
They do this to make the communication feel personal and to take advantage of previously established trust relationships to put the target in a stressful situation so that they are more likely to give up sensitive data or release funds.
Attackers know who you’re mostly likely to trust. Analysis of mailboxes protected by Sophos* revealed the roles most likely to be impersonated:
- 75% of emails impersonate the CEO or president (the highest-ranking individuals)
- 10% IT leadership (Director, VP of IT, or CIO)
- 5% financial leadership (the CFO or finance exec)
The remainder is made up of executive roles and C-suite leaders. What’s interesting is the uptick in medical professionals being impersonated: medical doctors and board-certified pediatricians now make up ~1-3% of individuals impersonated whereas previously they weren’t even on the radar.


People expect email scams, right?
When most people think of malicious emails they picture blatant requests for money, and excessive punctuation!!!
After analyzing thousands of messages we can see that, in reality, attackers are constantly evolving their approaches.
Their initial goal, of course, is simply to get the target to engage. Once the target’s on the hook, the attackers ramp up the pressure. Below are a couple examples of impersonation phishing messages blocked by Sophos Email.
Trust your inbox with Sophos’ latest email protection update
Can you remember what it’s like to work in an office? Where you could easily talk to real people? You could quickly pop your head into the Finance office and double check that they really wanted $250,000 wired to a supplier at 5pm on a Friday. With us all working from home lately, that’s not so easy.
That’s why Sophos mailbox protection through Sophos Email Advanced is so valuable. Earlier this year, we launch our first impersonation protection feature set, providing a setup assistant that integrates with AD Sync to automatically identify the individuals within an organization who are most likely to be impersonated.
Once set up, Sophos Email scans all inbound mail for display name variations associated with those users. Secondly, by analyzing header information, Sophos Email can identify brand spoofing and impersonation attempts.
The latest advancement for Sophos Email now uses advanced machine learning to detect targeted impersonation (or Business Email Compromise) attacks. Utilizing the Sophos-built deep learning neural network, our advanced ML capabilities analyze the message body content and subject lines of email messages to identify those conversations with suspicious content – specifically in relation to tone and wording used to identify unusual requests from a sender.
Superior phishing protection with Sophos Email Advanced
The level of phishing protection added to Sophos Email in this latest release offers incredible value, with simple controls that helping ensure protection is in place quickly.
Social engineering
Suspicious messages can be blocked, quarantined, tagged with a subject line, or have a warning banner added. Sophos scans all inbound email in real time, searching for key phishing indicators with SPF, DKIM, and DMARC authentication techniques and email header anomaly analysis. We also provide impersonation protection using content, display name, and lookalike domain analysis to identify impersonation attempts of a brand or VIP of an organization.
Malicious URLs and attachments
To protect against malicious URLs or attachments that may contain malware, Sophos provides real-time URL scanning and Time-of-Click URL rewriting to analyze any URL before it’s clicked. Then Sophos Sandstorm, our AI-powered cloud sandbox, detonates suspicious files to ensure malware never reaches the inbox.
User education
Finally, a great line of defense against email impersonation is intelligent cybersecurity awareness training. Sophos Email works with Sophos Phish Threat, our phishing simulation and training platform. Identifying users who have been warned or blocked from visiting a website due to its risk profile or replying to a spear phishing email, Sophos Email and Sophos Phish Threat can work hand in hand to seamlessly enroll risky users into targeted phishing simulations and training to improve awareness.
Start a no-obligation free trial of Sophos Email and Sophos Phish Threat from our website. Sophos customers who are already managing products through the Sophos Central platform can activate a free trial directly from their console: visit the More Products section in the main navigation to get started.
Sophos Central Phish Threat Manager
*Analysis of Sophos Email platform from January – April 2020.
